Was setting up a new FreeIPA sever for my homelab and found out that the default configuration in FreeIPA does not allow you to use VMware vSphere as a client as not being fully RFC4519 and missing some other LDAP class settings.
Lets go through the steps of setting up a new FreeIPA server. We are going to use the official ansible repositories and collection for this purpose.
For this article we have the following assumptions:
- Ansible host in the same subnet with the server that needs to be set up with FreeIPA.
- ssh connectivity without password (ssh key) to FreeIPA server
- FreeIPA server with CentOS 7 at freeipa.cloudalbania.com with minimum 1 Gb memory and 8Gb disk space
- you already have vCenter up and running
Preparing the Ansible host and FreeIPA repository
We are going to use the official ansible repository to install FreeIPA. On a host with ansible 2.9+ issue the following commands to install and setup initial FreeIPA server
$ git clone https://github.com/freeipa/ansible-freeipa.git $ cd ansible-freeipa $ echo << EOF > inventory/my-freeipa-server [ipaserver] freeipa.cloudalbania.com [ipaserver:vars] ipaserver_domain=cloudalbania.com ipaserver_realm=CLOUDALBANIA.COM ipaadmin_password=<STRONG PASS> ipadm_password=<STRONG PASS> EOF
ansible-galaxy collection install freeipa.ansible_freeipa -p ./
$ cat ansible.cfg [defaults] host_key_checking = False deprecation_warnings=False collections_paths = ./ roles_path = ./roles nocows=1
Installing FreeIPA
$ ansible-playbook -u root -i inventory/my-freeipa-server playbooks/install-server.yml
Configure FreeIPA for RFC4519 and vSphere
$ echo << EOF > vsphere_usermod.ldif
dn: cn=users,cn=Schema Compatibility,cn=plugins,cn=config
changetype: modify
add: schema-compat-entry-attribute
schema-compat-entry-attribute: objectclass=inetOrgPerson
-
add: schema-compat-entry-attribute
schema-compat-entry-attribute: sn=%{sn}
-
EOF$ echo << EOF > vsphere_groupmod.ldif
dn: cn=groups,cn=Schema Compatibility,cn=plugins,cn=config
changetype: modify
add: schema-compat-entry-attribute
schema-compat-entry-attribute: objectclass=groupOfUniqueNames
-
add: schema-compat-entry-attribute
schema-compat-entry-attribute: uniqueMember=%mregsub("%{member}","^(.*)accounts(.*)","%1compat%2")
-
EOFApply then with the following
$ ldapmodify -x -D "cn=Directory Manager" -f vsphere_usermod.ldif -W
$ ldapmodify -x -D "cn=Directory Manager" -f vsphere_groupmod.ldif -W
# ipa permission-mod "System: Read User Compat Tree" --includedattrs sn # ipa permission-mod "System: Read Group Compat Tree" --includedattrs uniquemember
$ kinit admin
Initial configuration for FreeIPA
- A bind user that will be used to bind to the LDAP server, we are using bind-user@cloudalbania.com
- An end user, in this case bzanaj@cloudalbania.com
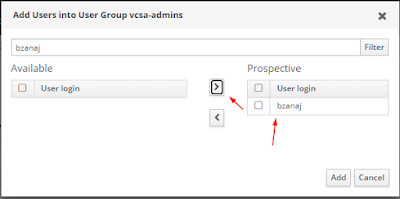
- Two LDAP groups that will be used to add our users to vcsa-admins and vcsa-readonly.
Configure vSphere Authentication for FreeIPA
In the vSphere GUI go in Admistration -> Single Sign On -> Configuration -> Identity Providers and then Add.
In the next screen enter the following details as shown in the screenshot below:
Note: I am not using a certificate to authenticate on the LDAP server as it is out of the scope of this article.
After you save this configuration and there are no errors then you can assign the groups in the
Permissions settings in Access Control
At the end we should see the following: